 Many of the businesses that Homeland Secure IT serves are using Trend Micro Worry-Free Business Security as their weapon of choice against malware and even spam. Once the product is loaded on their server and installed on their desktops, it will generally automatically download the security updates required to keep it current.
Many of the businesses that Homeland Secure IT serves are using Trend Micro Worry-Free Business Security as their weapon of choice against malware and even spam. Once the product is loaded on their server and installed on their desktops, it will generally automatically download the security updates required to keep it current.
However, every once in a while, Trend Micro will release an update to the entire system, which requires manual installation. This is keeps updates which might interfere with critical systems from being installed, and it also insures that new settings that require configuration are not put into the wrong state, crippling your network.
Currently, those who are running Worry-Free Business Security 9.0 Standard or Advanced, may be in need of two updates.
Service Pack 2, released in August, offers support for Windows 10 machines and enhanced ransomware protection.
Enhanced scan features can identify and block ransomware programs that target documents that run on endpoints by identifying common behaviors and blocking processes commonly associated with ransomware programs
In addition to the Service Pack 2 release, a Critical Patch was released on 8/31, which should also be applied to your Trend Micro Worry-Free Business Security servers.
Should you require assistance with this, Homeland Secure IT is happy to help! We can work with you in and around the Greenville SC area, or remotely if need be just about anywhere in the world!
If you are not using Trend Micro’s security products and would like more information about what it can do for your company, use our contact form or give us a call at 864-990-4748!

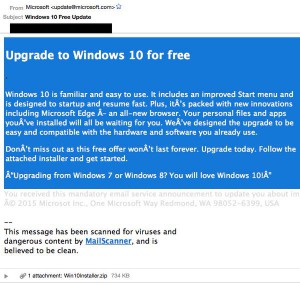 With all the excitement about Microsoft Windows 10 being a FREE update, some people signed up for the “Get Windows 10” promotion as prompted in their taskbar, to be put on a waiting list. So it’s not surprising that when an email comes in that looks legit, that someone might follow the link and attempt to install it.
With all the excitement about Microsoft Windows 10 being a FREE update, some people signed up for the “Get Windows 10” promotion as prompted in their taskbar, to be put on a waiting list. So it’s not surprising that when an email comes in that looks legit, that someone might follow the link and attempt to install it.


