Being in the computer service business, every day we are seeing more and more computers that have been compromised, whether they are Microsoft Windows, Apple Mac OS X, Linux, it doesn’t matter. Even iPhones and Androids are falling victim to various malware found as a result of blindly following links.
What can you do to help protect yourself, your computer and your private data? Use a little common sense and don’t just randomly click on every link you see.
Sometimes, a link can come to you through email, a Facebook message, or a wall post on Facebook, and it will appear to be from your best friend, or a trusted co-worker, but it was really sent from a malicious source.
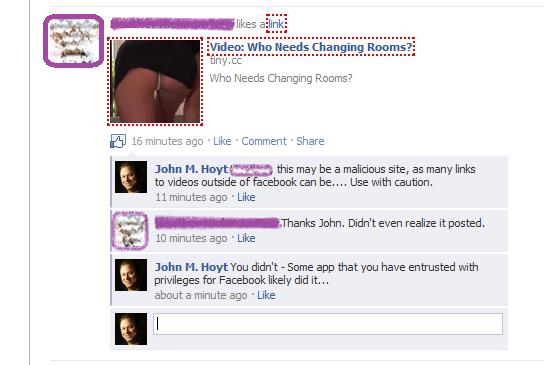
Here’s an example of a link posted on Facebook recently:
This is a typical “social engineering” attempt to get you to visit a malicious site.
It works like this: The mark will see the link on their best friend’s wall and because it looks appealing and came from Bob, it has to be good, so they click on it. The link loads a site that LOOKS like YouTube or some other video site. When they try to play the video, what happens next is sheer genius. They are told that a codec or other piece of software needs to be updated. Of course, they have gone this far, so they will almost always agree to install the software.
And THAT is where the magic takes place. Even if you are running anti-virus, many times, this malicious software is allowed to install because the A/V sees it as a “user initiated action” and simply gets out of the way and lets you perform the install. After all, you know what you are doing, right?
Now there is malicious software running which may do many things, from disabling the anti-virus, to loading key loggers that send every key typed on that computer to some site in Tracrapistan, or full access to the machine may be granted to a remote user, allowing them to use the exploited machine to send spam, distribute more bad software etc. Whatever takes place is surely not good. They are not defragging the hard drive and doing your taxes.
Then there’s email “Phishing”… Here’s what that looks like… Can you spot what is wrong?
There are a number of things wrong with the above email example… Most banks do not send you email warnings that you have been locked out of your account, and in my case, I don’t even have a Chase bank account…. But those are not the one tell-tale sign that will prove beyond a shadow of a doubt it is a phishing message or an attempt to coax you to a malicious website…
To see that, you need only hover over the link itself:
When you place your mouse over the link, without even clicking on it, your email client will generally display the actual link. This one points to http://ciamedia.be…. not even close to a Chase server. The perpetrator of this attempted phishing attempt didn’t even try. Sometimes they will register a domain that LOOKS like the source, such as http://www.chasesecuresite.com.
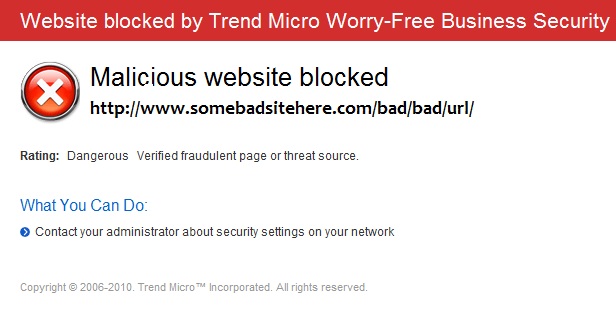
Again, if you are using current mainstream anti-virus software, such as Trend Micro Worry-Free Business Security or Trend Micro Titanium, every URL that you visit will be checked before allowing you to continue… Attempting to visit a malicious site will result in a dire warning displayed in your browser….
Above is the warning you will see in your browser upon visiting a fraudulent site if you are using Trend Micro Worry-Free Business Security …
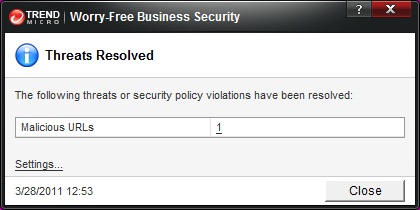
Then you will also see this warning pop up from your task bar:
Obviously, relying solely on your anti-virus software is not the wisest thing in the world… Safely browsing the web requires some common sense.
BUT, reliable and up to date anti-virus gives you an advantage that your unprotected brethren do not have. Especially for you Apple Mac OS X owners.
If you are looking for quality anti-virus, anti-malware, anti-spam software for your business or personal computer, we highly recommend Trend Micro… We are a Trend Micro partner and would love the opportunity to offer their fantastic products to you, whether you need only one install for yourself, or 1000 seats for your company. We not only sell it, but we support it, along with full computer, server & network service / repair in Greenville & Upstate SC!
Please email info@homelandsecureit.com or call 864.990.4748 for more information.